.lotep Files Virus – How to Remove It + Decrypt Files
This article aims to show you how you can remove .lotep Files Virus from your computer effectively. The steps in this post also aim to help you to try and restore files, encrypted by the .lotep ransomware.
Yet another version of STOP/DJVU ransomware variants has been recently detected. The ransomware’s main purpose is to encrypt your files, using the AES encryption cipher and then extort you into paying ransom to get them back. This ransom is usually in the form of BitCoin transfer of a huge sum of money. The .lotep variant of STOP ransomware also leaves behind a ransom note file, called _readme.txt, whose main purpose is to provide instructions to victims on how they can pay the ransom to the crooks. Read this article to fully understand how .lotep ransomware works and how to remove it and try to get back encrypted files.

Threat Summary
| Name | .lotep Files Virus |
| Type | Ransomware, Cryptovirus |
| Short Description | The .lotep files virus is a variant of STOP/DJVU ransomware family of viruses, whose main goal is to hold your files hostage until a ransom has been paid. |
| Symptoms | Files have the .lotep suffix and cannot be opened. The ransomware leaves behind a _readme.txtransom note. |
| Distribution Method | Spam Emails, Email Attachments, Executable files |
| Detection Tool | See If Your System Has Been Affected by .lotep Files Virus
Download
Malware Removal Tool
|

.lotep Files Virus – Update June 2019
The good news for all victims of STOP .lotep ransomware is that the security researcher Michael Gillespie cracked the code of this variant and released an updated version of his STOP ransomware decrypter.
So the moment you remove all malicious files and objects from your infected system you can enter our data recovery guide where you will find a download link for the free .lotep decryption tool and learn how to proceed with the decryption process.
Have in mind that the tool is designed to support specific offline IDs, so it may not be effective for all occasions of .lotep ransomware infections.

.lotep Files Virus – How Did I Get It and What Does It Do?
The .lotep files virus is a new variant of STOP ransomware. The variants before it, came out just last week, called .truke files virus, .neras files virus and .horon files virus.
The primary method of distribution that is used by the .lotep ransomware virus for infection could as well be via malicious e-mail attachments. These e-mail attachments aim to pretend to be seemingly legitimate files from the likes of:
- Invoices.
- Receipts.
- Banking documents.
- Delivery documentation.
- Work-related documents.
In the e-mails in which they are spread, they are often attached in .ZIP or .RAR archives and downloading the virus file, thinking it is a document is the main weapon the crooks use to infect you with malware, like .lotep files virus.
Another way to infect your computer, that is also used by ransomware developers is to mask the virus file of .lotep ransomware is to upload suspicious files on software download sites. There, the files may pretend to be legitimate types of files, such as keygens, cracks, patches, setups and other forms of files.
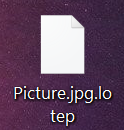
Once having infected your computer, the .lotep Files Virus may immediately begin to encrypt your files. The malware targets all documents, videos, images, archives, audio and other often used files and encrypts them with the AES (Advanced Encryption Standard) algorithm, which generates a unique assymetric decryption key. After the .lotep files virus encrypts your data, it leaves the files looking like the following:
In addition to encrypting files, the .lotep files ransomware also leaves behind it’s ransom note file, called _readme.txt. The ransom note has the following contents:
Don’t worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-pPLXOv9XTI
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
gorentos@bitmessage.ch
Reserve e-mail address to contact us:
gorentos@bitmessage.ch
Telegram
The ransom note’s main goal is to extort you into paying a hefty ransom so that the crooks can send you a decrypter for the .lotep files. The main idea behind this is for you to pay, which is not advisable in any way, because paying does not exactly guarantee you that you will get all your files back.
Furthermore, besides encrypting your files, the .lotep ransomware may also perform other virus activities on your computer, such as:
- Obtain your IP and MAC addresses.
- Obtain Administrator permissions.
- Obtain read and write permissions.
- Transfer files and information to the criminals’ C&C servers.

How to Remove .lotep Files Virus and Try to Restore Files
If you want to fully get rid of the .lotep ransomware from your computer, we strongly recommend that you follow the removal steps below. If you want to remove .lotep much faster and safer, we recommend that you skip the steps and go straight into downloading an advanced malware removal software. Such professional anti-malware tool has been designed to take care of threats, like .lotep ransomware by removing all of the .lotep virus files from your computer.
To try and restore .lotep encrypted files, we would strongly recommend that you try the alternative file recovery options we have added underneath, at least until researchers release a decrypter. Until then, we recommend backing up your files and checking this article for new developments that are about to come.
Bonus: Video containing step-by-step removal and file recovery instructions for threats, like .lotep Files Virus:
Preparation before removing .lotep Files Virus.
Before starting the actual removal process, we recommend that you do the following preparation steps.
- Make sure you have these instructions always open and in front of your eyes.
- Do a backup of all of your files, even if they could be damaged. You should back up your data with a cloud backup solution and insure your files against any type of loss, even from the most severe threats.
- Be patient as this could take a while.
Step 1: Boot Your PC In Safe Mode to isolate and remove .lotep Files Virus
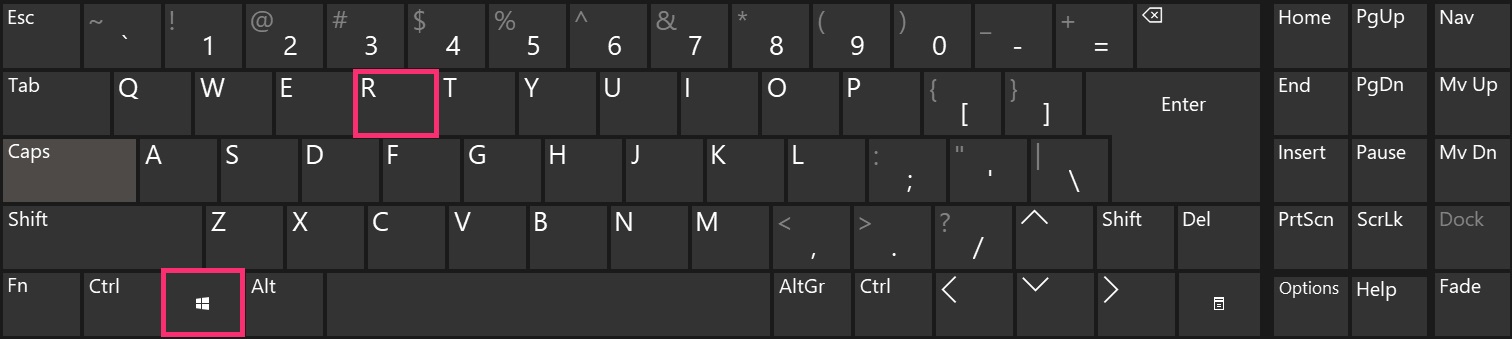


Step 2: Clean any registries, created by .lotep Files Virus on your computer.
The usually targeted registries of Windows machines are the following:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
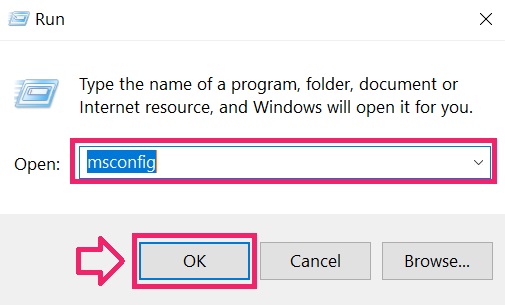
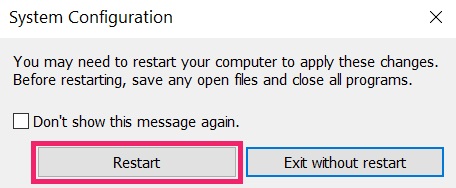
You can access them by opening the Windows registry editor and deleting any values, created by .lotep Files Virus there. This can happen by following the steps underneath:
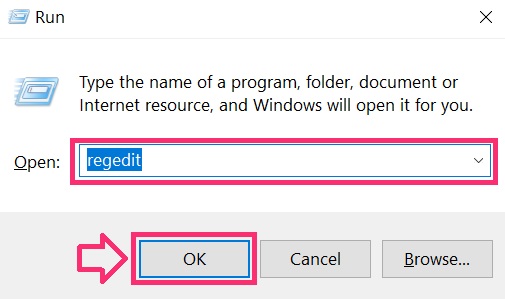
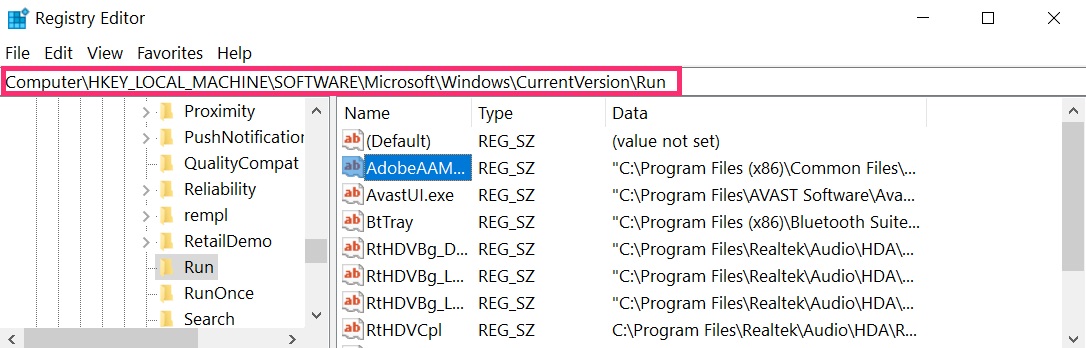
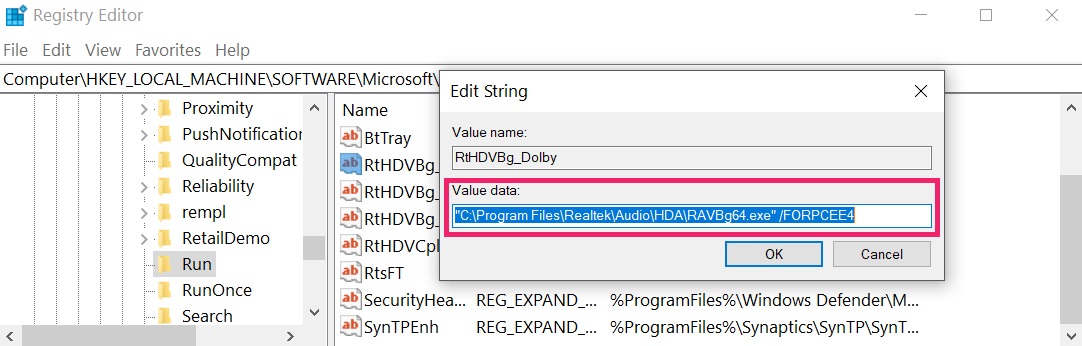 Tip: To find a virus-created value, you can right-click on it and click “Modify” to see which file it is set to run. If this is the virus file location, remove the value.
Tip: To find a virus-created value, you can right-click on it and click “Modify” to see which file it is set to run. If this is the virus file location, remove the value.
Step 3: Find files created by .lotep Files Virus
 For Windows 8, 8.1 and 10.
For Windows 8, 8.1 and 10. For Windows XP, Vista, and 7.
For Windows XP, Vista, and 7.
For Newer Windows Operating Systems
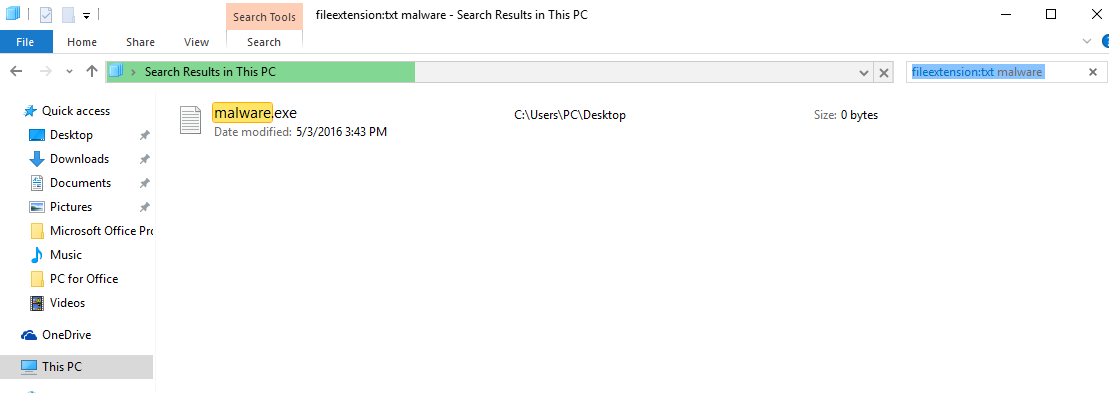
1: On your keyboard press + R and write explorer.exe in the Run text box and then click on the Ok button.
2: Click on your PC from the quick access bar. This is usually an icon with a monitor and its name is either “My Computer”, “My PC” or “This PC” or whatever you have named it.
3: Navigate to the search box in the top-right of your PC’s screen and type “fileextension:” and after which type the file extension. If you are looking for malicious executables, an example may be “fileextension:exe”. After doing that, leave a space and type the file name you believe the malware has created. Here is how it may appear if your file has been found:
N.B. We recommend to wait for the green loading bar in the navination box to fill up in case the PC is looking for the file and hasn’t found it yet.
IMPORTANT!
Before starting “Step 4”, please boot back into Normal mode, in case you are currently in Safe Mode.
This will enable you to install and use SpyHunter 5 successfully.
Before starting “Step 4”, please boot back into Normal mode, in case you are currently in Safe Mode.
This will enable you to install and use SpyHunter 5 successfully.
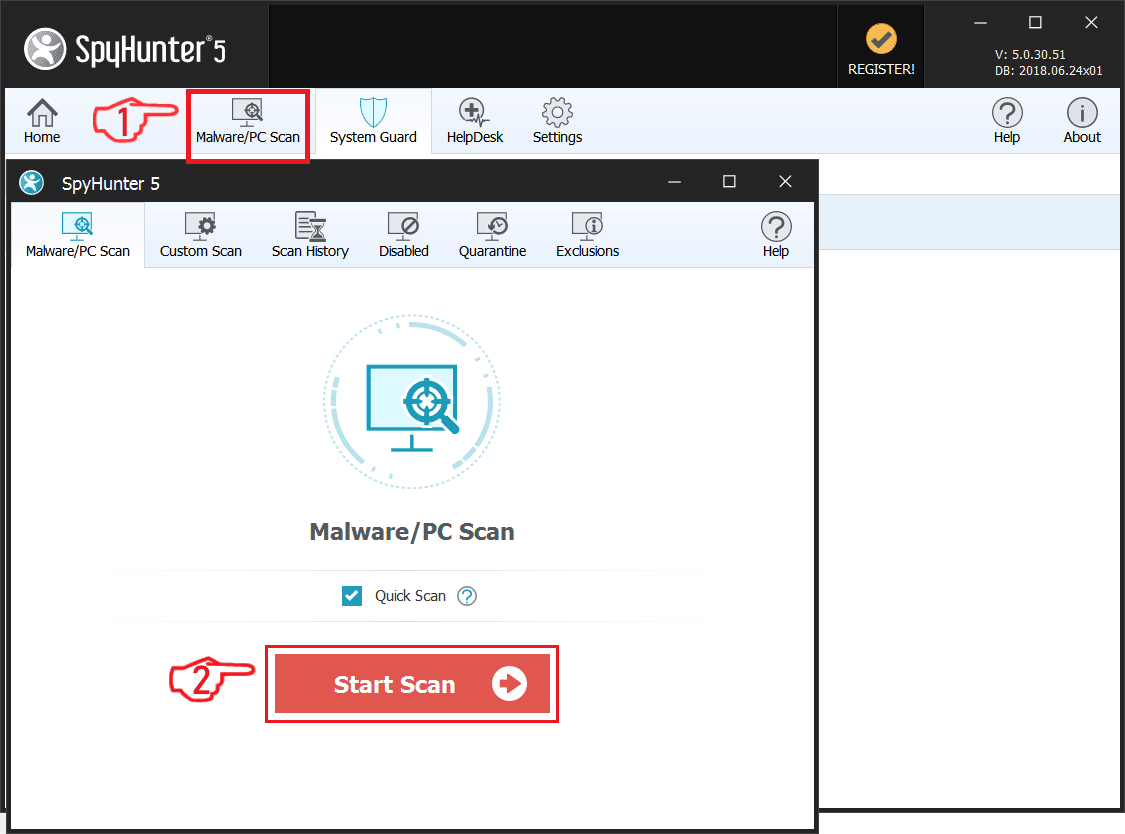
Step 4: Scan for .lotep Files Virus with SpyHunter Anti-Malware Tool
Step 5 (Optional): Try to Restore Files Encrypted by .lotep Files Virus.
Ransomware infections and .lotep Files Virus aim to encrypt your files using an encryption algorithm which may be very difficult to decrypt. This is why we have suggested several alternative methods that may help you go around direct decryption and try to restore your files. Bear in mind that these methods may not be 100% effective but may also help you a little or a lot in different situations.
Method 1: Scanning your drive’s sectors by using Data Recovery software.
Another method for restoring your files is by trying to bring back your files via data recovery software. Here are some suggestions for preferred data recovery software solutions:
Another method for restoring your files is by trying to bring back your files via data recovery software. Here are some suggestions for preferred data recovery software solutions:
- Stellar Data Recovery Technicians License(Pro version with more features)
- Stellar Windows Data Recovery
- Stellar Photo Recovery
Method 2: Trying Kaspersky and EmsiSoft’s decryptors.
If the first method does not work, we suggest trying to use decryptors for other ransomware viruses, in case your virus is a variant of them. The two primary developers of decryptors are Kaspersky and EmsiSoft, links to which we have provided below:
If the first method does not work, we suggest trying to use decryptors for other ransomware viruses, in case your virus is a variant of them. The two primary developers of decryptors are Kaspersky and EmsiSoft, links to which we have provided below:
Method 3: Using Shadow Explorer
To restore your data in case you have backup set up, it is important to check for Volume Shadow Copies, if ransomware has not deleted them, in Windows using the below software:
Method 4: Finding the decryption key while the cryptovirus sends it over a network via a sniffing tool.
Another way to decrypt the files is by using a Network Sniffer to get the encryption key, while files are encrypted on your system. A Network Sniffer is a program and/or device monitoring data traveling over a network, such as its internet traffic and internet packets. If you have a sniffer set before the attack happened you might get information about the decryption key. See how-to instructions below:





No comments